

2017-05-09 10:24:00
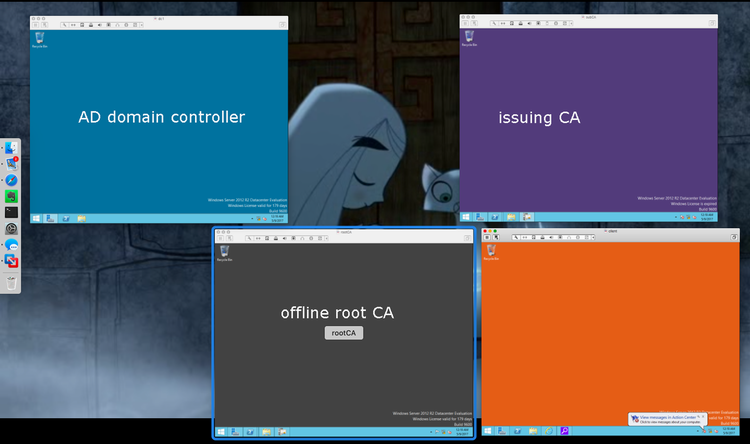
A bit over a year ago I first started working with Microsoft's Active Directory, integrating it with BoKS Access Control. At the time, I was impressed by Windows Server 2012 and 2016 and the ease with which I could set up an AD forest with users.
I'm now learning how to build a two-tier PKI infrastructure, after seeing them in action at various previous clients. I've been on the consuming end of PKI for years now and I thought it was time to really know how the other end works as well! I must say that I love Microsoft's generosity when it comes to documentation! Not only do they provide proper product docs, but they also have online tutorials in the form of TLGs: test lab guides. Using these, you can self-teach the basics of a subject, and then build up from there.
The 2012 Base TLG helps you build a basic AD forest of systems. I can follow it up with the two-tier PKI infrastructure TLG, which helps me set up an offline root CA, and an issuing CA, along with automatically enrolling any new systems in the networkt that need SSL certs. Awesome!
I'm similarly extatic about the performance of my Macbook Air. It's a tiny, super-portable system, but it still doesn't balk at running my usual applications plus four full-fledged Windows Server 2012 hosts. Nice!
EDIT:
Ammar Hasayen also did a nice write-up, which appears to be based upon the two-tier PKI TLG but which adds additional details.
Also, Microsoft also offer a third great resource, their MVA: Microsoft Virtual Academy. They also have a course on two-tier PKI with ADCS.
kilala.nl tags: work, windows,
View or add comments (curr. 0)
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.