

2017-10-29 12:56:00
I used Sander van Vugt's EX413/LPI3 video training to prep for my EX413 exam and expanded upon all that information by performing additional research. All in all, I've spent roughly sixty hours over the past five weeks in order to get up to speed. Over the course, over fifty pages of notes were compiled. :)
I've extract all the really important information from my notes, to make this seven-page EX413 cheat sheet. I hope other students find it useful.
Of course, this is NO SUBSTITUTE for doing your own studying and research. Be sure to put in your time, experimenting with all the software you'll need to know. The summary is based on my own knowledge and experience, so I'm sure I've left out lots of things that other people might need to learn.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-10-28 08:53:00
In my test networks at home I've often run into issues with NetworkManager or dhclient messing with my network settings, most importantly the DNS configuration. Judging by the hundreds of StackExchange and other forum posts to the same effect, I'm certainly not alone. The fact that this seems like such a newbie problem just makes it all the more annoying.
I've tried many changes, based on those forum discussions, such as:
And funnily enough, things would still be changing my /etc/resolv.conf every time networking was restarted.
Turns out that I am in fact making a RedHat-newbie mistake! I'm stuck in my old ways of manually micro-managing specific settings of a Linux box. I'm so stuck that I've forgotten my lessons from the RHCSA certification: system-config-network-tui.
That tool is great at resetting your network config and overwriting it with the exact setup you want. It helps clear out any settings in odd places that might lead to the continuous mucking about with your settings.
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
2017-10-08 10:29:00
For the third year in a row I competed in the PvIB CTF "Pen.test event", a Jeopardy-style CTF where contestants race to solve puzzles and small hacking challenges. Last year I didn't fare very well at all, but this time aroud things went great! The crowd was nice, my table companions were cool, it was great talking to Anko again and the DJ played awesome beats. I had a blast!
Around 1.5 hours into the competition I went to stretch my legs and get a drink, enjoying the fun we were having. Looking around, sipping on my cola I noticed something odd about the scoreboard! When I'd managed to grab my phonecam I'd already been surpassed by one team, but for at least a short while I'd managed to be in #4 out of the pack of 51 contestants. In the end I finished somewhere halfway , because greater minds than mine managed to keep on scoring points :)
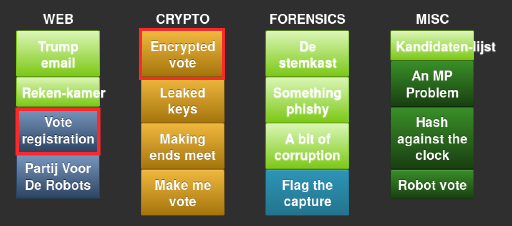
Like before, the challenges were divided into various categories (shown above) and ranked from easy to hard, resulting in different scores per item. I finished the night with 100.000 points (3x10e3, 2x10e4, 1x10e3). I was so, so close on another 10k and 30k points which is why I stuck around until the very last minute!
Web:
Learning on the go was hella fun! I got to renew my experience with CURL calls and XML data and learned new things about SOAP. Nice!
Crypto:
Cracking crypto never was my strong point ;)
Forensics:
Fun challenges! Not too hard so far.
Misc.:
What a great evening! Better yet, on the way home I managed to get on the Slam! night show and I won a DAB+ radio for our home! :D Awesome-cakes!
View or add comments (curr. 0)
2017-10-04 18:13:00

We've just bought a new laser printer, mostly for my daughter's schoolwork. Installation was a snap as both Windows and MacOS have made it a fool-proof process. MacOS even gave me a button labeled "Visit printer website"! Of course that's gonna pique my interest!
Yup, the HP Laserjet Pro M203dn (as it's fully named) has a wonderfully helpful web interface! By default, there's no username or password, there's no login prompt whatsoever. Just open for everyone to browse. Which is where I stumble upon the screenshot I'm showing above. Of course the SNMP community strings default to public/public. Why not? But who in the seven hells decided to make that SNMP daemon -writable-?! That's asking for trouble!
... aside from the "no username or password on the admin panel" of course. Ye gods! O_o
Oh and of course the certificate on the https web server was not signed by HP's CA. Because of course I wouldn't want to verify that nobody messed with the firmware or the certs on the printer.
... *checks around* Yep, HP also don't have a bug bounty program. =_=
kilala.nl tags: sysadmin,
View or add comments (curr. 1)
2017-10-01 21:44:00

In preparation for my upcoming EX413 examination, I'm mucking about with FreeIPA.
FreeIPA is a easy-to-setup solution for building the basis of your corporate infrastructure on Linux. It includes an LDAP server, it sets up DNS and a CA (certificate authority) and it serves as Kerberos server. Basically, it's a light version of Active Directory, but targeted at Linux networks. Of course Linux can use AD just fine, but if you don't have AD FreeIPA is the next best thing.
IPA has come a long way over the past ten years. It might still not be fully featured, but it certainly allows you to setup a centralized RBAC platform, not unlike the BoKS product range I've worked with. BoKS offers more functionality (like a password safe and the possibility to easily filter SSH subsystems like allowing SCP or SFTP only), but it's also far from free.
I'm currently doing exactly what EX413 exams want you to be able to do: install a basic FreeIPA environment, with some users and some centralized SUDO rules. It's the latter that was giving me a little bit of a headache, because I had a hard time figuring out the service account to use for the bind action. Sander van Vugt's training video refers to the service account uid=sudo,cn=sysaccounts,dc=etc,dc=ex413,dc=local, which does not appear to exist out of the box.
This set me off one a foxhunt that lasted 1.5 hours.
Because this is a sandbox environment, I've set up one account as both the SUDO bind user in /etc/sudo-ldap.conf and in the ADS user interface. Both now work swimmingly! I can "sudo -l" as a normal user and I can mess around the LDAP tree from the warmth and comfort of my MacOS desktop :)
EDIT:
Well I'll be a monkey's uncle! That little rascal of a UID=sudo was hiding inside LDAP all along! I guess I really did make a mistake in my initial ldappasswd command :D Well, at least I learned a thing or two!
EDIT 2:
FOUND IT! The OID I showed up top has an "s" too many! I wrote "sysaccountS", while it's supposed to be "sysaccount". Ace! That's going to make life a lot easier during the exam :)
kilala.nl tags: work, sysadmin,
View or add comments (curr. 0)
All content, with exception of "borrowed" blogpost images, or unless otherwise indicated, is copyright of Tess Sluijter. The character Kilala the cat-demon is copyright of Rumiko Takahashi and used here without permission.